We’ve already seen that one of the ways to decide if the risks are acceptable or not is the value of information.
Let me remind you that the value is computed on four dimensions:
- the intrinsic value: what it cost to fetch for the information, to acquire it, to collect it, to manage it, to care for it;
- the usage value: what you can do with it;
- the attraction value: how much “the others” are interested in it – to know it, to take it from you or to make it unusable for you;
- the loss value: what you can’t do any more if the information doesn’t meet your expectations.
Another means – that may also help you to determine the usage value – is to use a management tool.
We saw two weeks ago how the B.S.C. could help you to build your Security Action Plan.
To finalize the risk assessment, we can use the SWOT (http://en.wikipedia.org/wiki/SWOT_analysis).
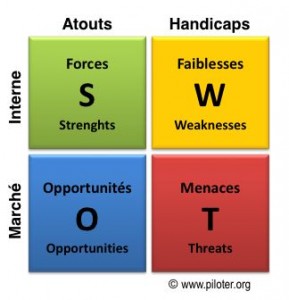
The SWOT
The SWOT, a key tool in Value Management aimed to propose a strategy, puts Strengths and Weaknesses in the internal factors while Threats and Opportunities are considered as external. Positive and negative elements, internal or external elements (to the organization or the security activities) that one can try to balance.
Strengths
Strengths are:
- Successes you already achieved with the information and the processes applied to them;
- Your internal and external proofs of the effectiveness of your security, your achievements;
- A combination of factors that support the achievement of your objectives.
Strengths are the risks you have already effectively covered.
Strengths should be preserved to ensure success on the long term.
Weaknesses
Weaknesses are:
- Your business or personal failures and shortcomings with regards to the internal and external requirements referring to information and their handling;
- The internal and external constraints that make your successes more difficult;
- Your security vulnerabilities, that’d help threats to concretize in negative events or could prevent you to reach your objectives.
Your acceptable risks that require to be watched are weaknesses.
The Weaknesses should be resolved to ensure success on the long term.
Opportunities
Opportunities are:
- The objectives you’re aiming at with the information and their handling;
- Your positive moves in security that became a foundation for your evolution (remember the dimension ‘Operational Excellence’ of the B.S.C.);
- The factor and tendencies that contribute (necessary but not sufficient) to achieve your business, personal or security objectives.
Existing security solutions and applying recognized good practices are Opportunities.
Opportunities can solve Weaknesses, increase Strengths and – if successfully exploited – help achieving your objectives.
Threats
Threats are:
- The factor and tendencies that are obstacles to reaching your objectives, that don’t allow you exploiting the opportunities;
- All negative elements of the external context, with e.g. the number and strength of your competitors;
- The virulence of the attacks you’ve already suffered or that affect competitors, that target your objectives, your business your information system – or these similar to yours.
Remind you that it doesn’t only happen to the others!
Threats are also the unacceptable risks you haven’t covered yet.
Threats build on Weaknesses and reduce the Strengths.
How to use the SWOT?
The table should be easy to fill in if you followed the risk management process: context analysis and risk analysis. All information is at hand.
Information value is a parallel element. Attraction Value can be a Threat, Usage Value is an Opportunity, Loss Value is a Weakness and Intrinsic Value is a Strength.
Strategies
The specificity of the SWOT allows you to select one out of four strategies you’ll put in action with the B.S.C.
- S-0: Exploit your Strengths to take profit of your Opportunities (when the Weaknesses and Threats are under control);
- S-T: Exploiting the Strengths to counter the Threats;
- O-W: Use the Opportunities to cover the Weaknesses;
- W-T: Cover Weaknesses and counter the Threats.
Your choice of strategy depends on the balance – or unbalance – of the four factors and can be as variable as the context. Hence, this choice is won’t be definitive.
The “precaution principle” recommends to first use W-T, S-T and O-W strategies, especially if these factors are prominent.
You see, using ‘alien’ tools isn’t difficult.
Do you have questions? How do you see these tools? Do you use other tools and techniques others may benefit of? Share it with us…
See you soon, more secure with your information
Jean-Luc
Google+

Way cool! Some extremely valid points! I appreciate you penning this post and the rest of the website is very good.