We already saw that our Security Action Plan should contain solutions to cover important and urgent risks. According to the preponderance of the Potentiality of occurrence of risks or their Consequence, the most relevant solutions will be preventive, reactive or corrective – or any combination of these.
We also studied the eight domains in which risks and solutions exist.
But if this can suffice for simple and domestic (or private) situations it is highly possible that enterprises (Small and Medium Enterprises, for example, but surely the big ones) will need to go much further.
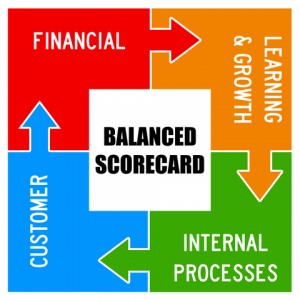
What’s the B.S.C.?
Norton and S. Kaplan stated that enterprises mainly focus on financial aspects and disregard the others aspects while evaluating their strategies. In 1992, they create the Balanced Scorecard (BSC) as a tool to balance the finances.
The B.S.C. tends to ensure the (financial) Goals, the Client’s satisfaction, the Internal capability and the Future Capability are adequately taken into account.
The B.S.C. consists in four quadrants or perspectives
- Client = How can we satisfy them?
- Learning and Growth = How can our innovation capability evolve to enhance value creation and maturity?
- Sustaining business = What tells to them? How can we achieve operational excellence?
- Financial = How to preserve and provide value to our processes?
Each quadrant defines objectives, controls (or solutions), measurable targets and initiatives to reach them.
It’s not a tool to select a strategy, but it allows to completing and implementing the strategy. Each quadrant has an influence on its neighbours as to create a virtuous circle. If one is empty or weak, it will freeze or weaken the dynamics.
The Security B.S.C.
In the beginning of the 2000’s, the famous MIT (Massachusetts Institute of technology) thought it would be nice to use the B.S.C. for the IT department. I discovered that information security could take benefit of their discoveries, without difficulties.
The only difference with the original B.S.C. holds in the perspective: the ‘clients’ are all these (mainly internal to the organization) who use the IT or security solutions.
You’ll remark that the two first categories focus on the object and use of security, while the two last concern the security itself and its actors.
Business orientation
How to sustain the business needs and requirements?
This contains the study of the business and information processes, the evaluation of the value of information and the legal compliance.
Service to clients
How can the client take profit of our services and be satisfied?
We find here awareness and training, appropriate response to incidents and, mainly, the design of transparent, non-constraining and easy-to-use solutions, along with all what allows the user to take his/her responsibilities.
Future orientation
How can security evolve with the needs and the ever-changing threats and risks?
This contains risk management and the permanent education of the security personnel.
Operational excellence
How are we mastering the security processes?
This concerns the search for solutions ‘secure by design’ with the best cost/effectiveness ratio and solutions that take into account user’s needs and constraints.
How do we use it?
- Put your security controls and solutions in each category (only one possibility)
- Verify if there is sufficient balance between the four categories
- Complete the void or light-fed category (or categories) with new controls.
You need to go back to your risks and see what you can find to feed the incomplete categories. A minimum of imagination suffices…
You’ll agree that imagination may rapidly fall short. It’d be nice to dispose of a Referential of controls provided by a trusted body. However, these documents aren’t easy to access, whatever the language. You have to know where to fetch and how to manipulate these documents that are frequently big.
I’m preparing you a list based on free sources (in French, English and German). I just ask you some time to gather this.
What are your techniques to ensure your security controls are complete and coherent? Why not sharing these with us?
See you soon, safer with your information
Jean-Luc
Photo credit : http://sicoraconsulting.com/balanced-scorecard/ © Icefields | Dreamstime.com – Balanced Scorecard Photo
Google+