Cryptography existed far before the computer. The ENIGMA* case during the Second World War is a good example. The first uses date back to more than 2000 years.
To hide the meaning of a text – and doing so making it unintelligible and unexploitable – we have two options: coding and cyphering.
Coding
Coding is a technique to replace a text by a code, character by character. The foreign, strange or antique alphabets are relevant: Chinese, Arabic, Sanskrit, cuneiform, hieroglyphic, Maya, etc. It is not an obstacle for those who know these languages or these codes. Only Mayan hieroglyphs are still resisting translation.
Templars had their own code, which isn’t a mystery anymore for long.
The techniques to create strong passwords use these coding methods.
Cyphering is much more coherent and strong.
Cyphering
It is a technique to replace a text by a succession of classical characters, but totally unintelligible. Three modes have been used for centuries: transposition, substitution and mixed.
Transposition
You move the letters in a defined fashion: the key.
The scytale* was of this type. One fabric or leather band is rolled around a stick whose diameter is the key. The message is then written horizontally, each letter on a successive spire.

You have the same effect when you write the message in a table with ‘x’ columns.
THE SHIRT becomes T*IHSREHT (key = 3).
Substitution
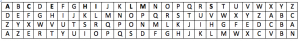
You replace a letter by another: 1° the one next to it on the keyboard, 2° 4 letters away in the alphabet, or 3° the same position in a reversed alphabet. Smart people used a mixed up alphabet (such as the succession of letters on an azerty computer keyboard, 4°).
The key is the mode of replacement.
THE SHIRT becomes 1° YJR DJOTY, 2° WKH VKLUW, 3° GSV HSRIG or 4° MIT LIOKM.
The ‘Caesar cypher*’ was of this type.
Mixed
One uses a precise sequence of moves and replacements.
All current secret key cypher systems on computers use this complex mode. The complexity is increased by the length of the key … 128, 256 or 512 bits (equals 16, 32 or 64 characters – alphanumeric, symbols and punctuation included).
They are identified by names such as: DES, 3DES or EAS followed 128, 256 or 512.
Remark that the time needed to decipher when you don’t know the key requires consequent resources. As the capability of computers is multiplied by two each year, the decipher time is divided by two. This still leaves the current systems safe for numerous years.
The key
The single element needed to both cypher and decipher is the key. We use the terms of Symmetric encryption. The protection of the key is obviously crucial. Ti’s the reason why the terms ‘SECRET KEY systems’.
All those who are authorized to decipher the message must receive the key that must be managed and communicated in a secure way. It is recommended to send the key and the message through different means or channels.
The problem is partially solved by determining a precise lifetime for the keys: from several weeks to… a few hours. Le ‘Book of codes’ is then the object to be found.
What can you do?
Usage
Protection of documents (for example the list of passwords), files (your invoices) or a whole hard disk. Secret key cryptography ensures the confidentiality – for a time sufficient so that the information has lost most of its value.
This mode also allows detecting the integrity problems as each modification of a character renders the deciphering incoherent the whole word. The selected technique can also prevent the deciphering of the remaining of the message.
Solutions
As the cyphering and deciphering are fastidious – mainly for long messages – use computer solutions. The following links give you ideas for free available solutions.
http://www.gfi.com/blog/the-top-24-free-tools-for-data-encryption/
http://lifehacker.com/five-best-file-encryption-tools-5677725
Small trick
You surely use some compressor-decompressor (e.g. ‘Zip’). It’s easy
- Compress the file and give it a typical name
- Replace the extension (.zip) by another you rarely use (.gif); the standard tool for this extension will return an error
- If necessary to isolate them, put these files in a special directory so you can more easily find them back.
To decipher…
- Find the interesting file
- Replace the .zip extension
- Decompress the file.
So… start using them! It’s easy, cheap and it allows you preventing a lot of troubles.
I hope experts will forgive me to having simplified to the extreme…
If you want to know more, look on the Internet for the expressions marked by an *.
See you later, safer with your information.
Jean-Luc
Google+